Phishing is the fraudulent practice of sending messages purporting to be from reputable companies in order to induce individuals to reveal personal information, such as passwords and credit card numbers. The scammers trying to get your information will present themselves, as banks, insurance companies, IT departments and for recyclers they may even disguise themselves as potential buyers. Many people have become aware of these types of scam emails, but phishing attempts are not just limited to emails.
Recently, an ISRI member was the target of a phishing attack where the scammer called the company, offering to buy high temperature alloys such as tungsten carbide at very attractive prices. The scammer did not take information on the phone but directed the member to a website to enter their credentials. The situation seemed odd, and the member decided to do some research, which revealed that the information on the website was fabricated; the address listing their warehouse did not exist on Google maps. The phishing attack was averted because the member took a moment to stop, think about the situation and do some research. This attack is a variation of the two-step cyberattack:
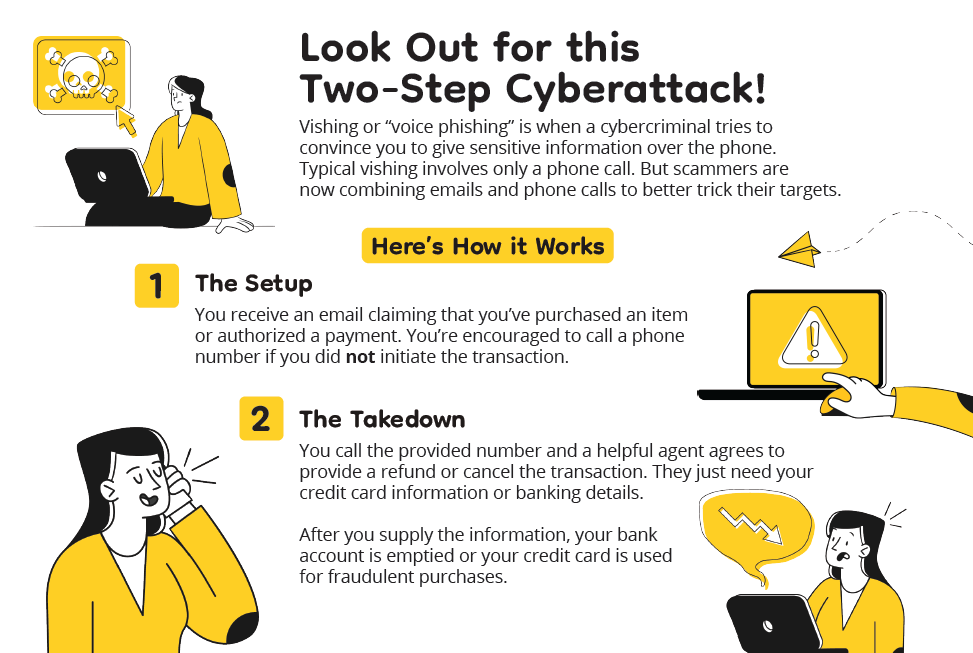
Graphic Courtesy of KnowBe4
What You Can Do
- Remember, phishing attempts can take multiple forms: phone calls, emails, text messages, etc. Unsolicited calls, emails or text messages are red flags.
- Never give any information until you have confirmed you are dealing with a reputable buyer or company. Pressure to respond quickly is a big red flag.
- Never open any attachments in an email or click on a link until you have confirmed you are dealing with a reputable buyer or company. Files like PDFs can contain malware that can steal your information, lock you out of your own computer network or worse infect computers and machines on your network.
- Be careful who you decide to do business with. Do as much research as you can. You can start by using tools like the ISRI member directory to look them up. Research the company name and address. Confirm that it exists with tools like Google Maps.
- If an offer is too good to be true, it usually is. Scammers take advantage of the fluctuating market and economic downturns, offering incredible prices for commodities that are not selling well.
- Sometimes scammers will use the cover of companies you have dealt with in the past. In these cases, call the customer service number you have used in the past with this company and confirm that it was actually them contacting you.
What to Look for in a Phishing Email
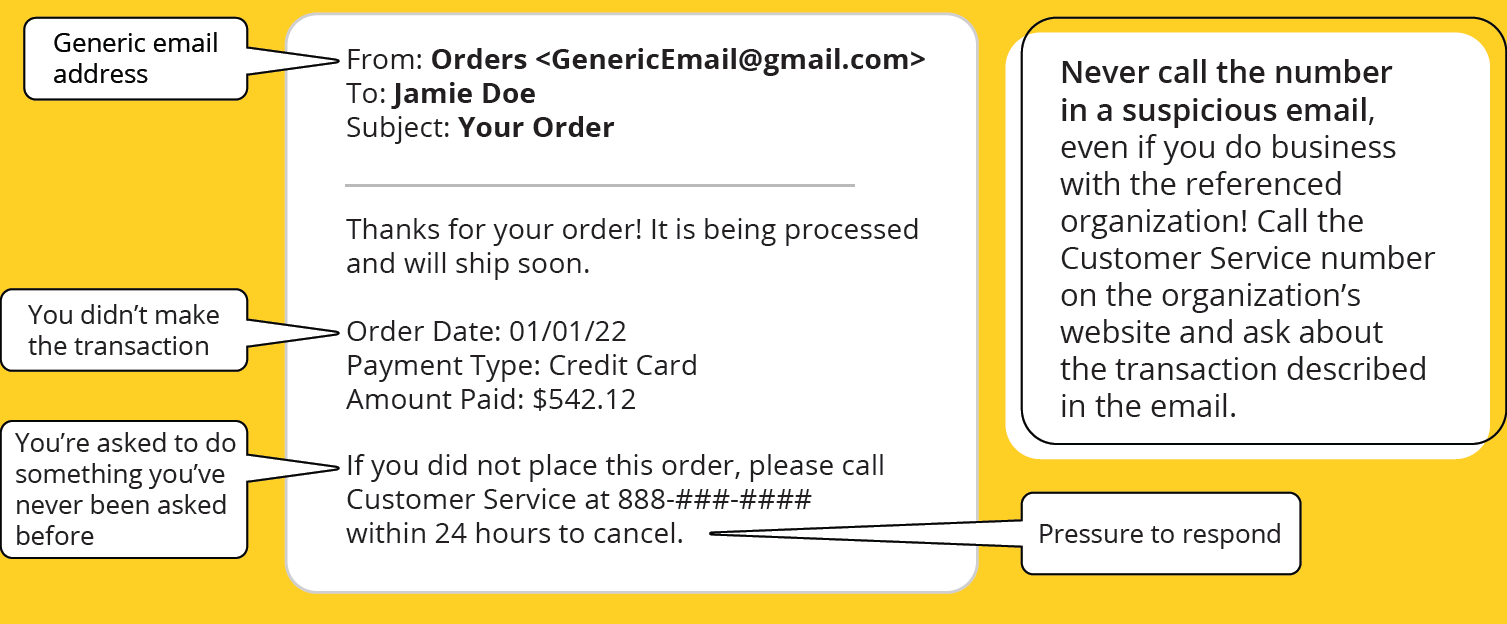
Graphic Courtesy of KnowBe4










